
Don't fall for another phishing attack. More than 96% of phishing attempts arrive by email. Phishing is a threat to every organization across the globe.
Given its cheap cost and high success rate, phishing is one of the most common scams across organizations today. The most common type of phishing attack involves a criminal posing as a high-level executive who will then send an email message to an employee with access to a desired system or information. Phishing email attacks leveraging COVID-19 were very successful in 2020, but a year later people have become more savvy against these attacks and those subjects have much less success. 'Spear Phishing' emails purporting to come from HR and security-related notifications are now on the rise.
What is Phishing?
Phishing is the process of attempting to acquire sensitive information such as usernames, passwords and credit card details by masquerading as a trustworthy entity using bulk email which tries to evade spam filters.
Emails claiming to be from popular social web sites, banks, auction sites, or IT administrators are commonly used to lure the unsuspecting public. It's a form of criminally fraudulent social engineering.
So, why does phishing keep happening? It's because people continue to fall for it! Organizations should have ongoing security training and education to prevent their employees from being easy targets. It is imperative that all employees in an organization understand what a phishing email looks like and how to avoid becoming a victim. There are a number of free online phishing tests available to you and your employees, Rhyme can also help develop a test to help educate your employees.
Learn more about phishing from the teams at CYBER.ORG and the Cybersecurity and Infrastructure Security Agency (CISA) in the video below.
Top five types of data stolen in phishing scams:
- Credentials (passwords, usernames, pin numbers)
- Personal data (name, address, email address)
- Internal data (sales projections, product roadmaps)
- Medical (treatment information, insurance claims)
- Bank (account numbers, credit card information)
Top tips to prevent phishing scams:
- Educate all employees about phishing in general and spear phishing in particular.
- Review the email address of senders and look out for impersonations of trusted brands or people.
- Use strong, unique passwords. Better yet, use a phrase instead of a word. Use different passwords for each account. Use a mix of letters, numbers and special characters.
- Never take an email from a familiar source at face value. If it asks you to open a link or attachment, or includes a threat to close your account, think twice.
- If an email contains a link, hover your cursor over the link to see the web address (URL) destination. If it's not a URL you recognize or if it's an abbreviated URL, don't open it.
- Consider a verbal confirmation by phone if you receive an email from a client or coworker requesting sensitive information or other requests that seem odd to you.
- Use security software to help defend against malware, viruses and known phishing sites and update the software automatically.
Top Phishing Social Media Email Subjects
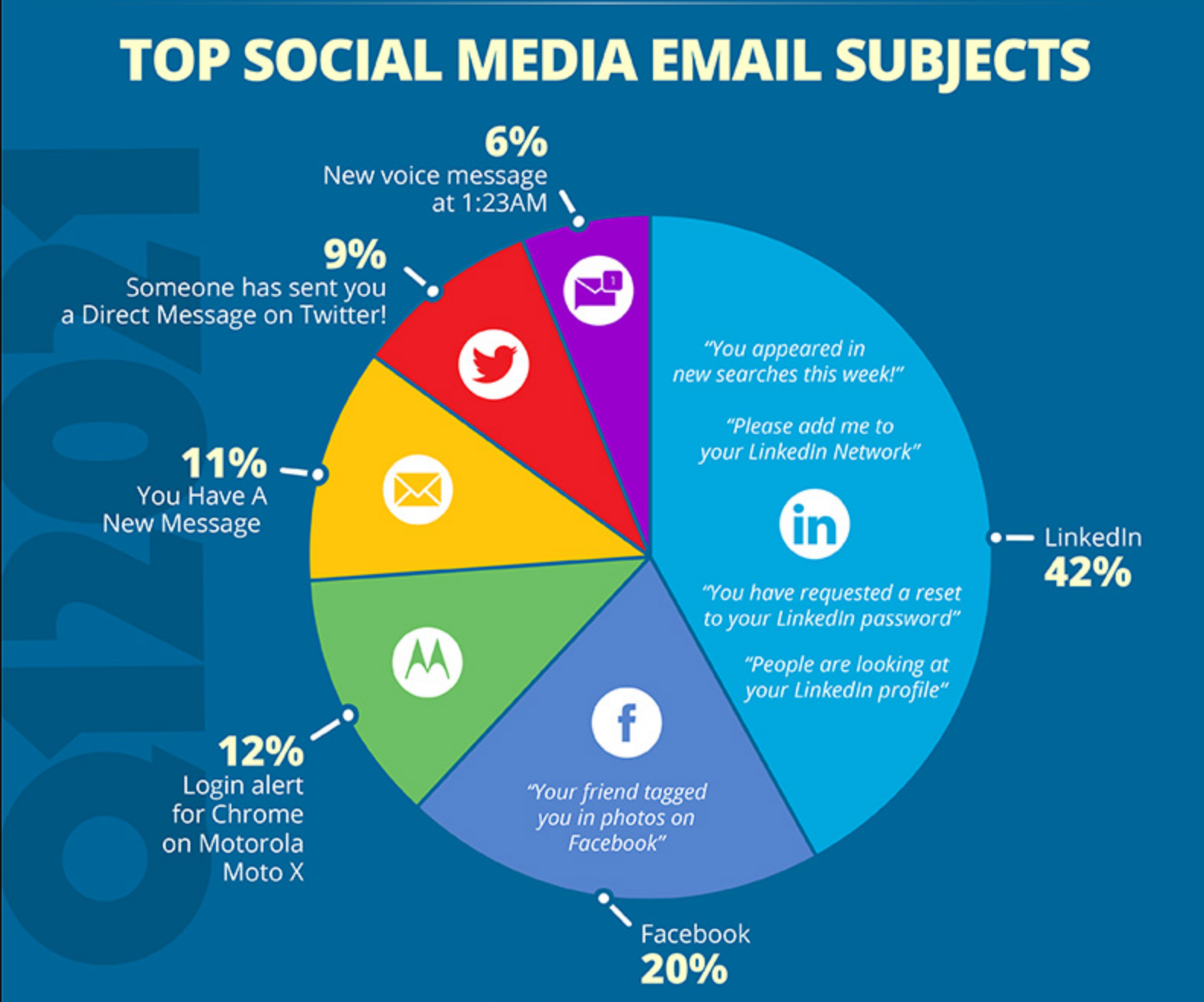 LinkedIn'You appeared in new searches this week!', 'Profile Views', 'Add Me', 'Reset password' (42%)
LinkedIn'You appeared in new searches this week!', 'Profile Views', 'Add Me', 'Reset password' (42%)- "Your friend tagged you in photos on Facebook" (20%)
- Login alert for Chrome on Motorola Moto X (12%)
- You have a New Message (11%)
- "Someone has sent you a Direct Message on Twitter!" (9%)
- New voice message at 1:23 AM (6%)
Key Takeaway
LinkedIn phishing messages have dominated the social media category for the last few years. Users may perceive these emails as legitimate since LinkedIn is a professional network, which could pose significant problems because many LinkedIn users have their accounts tied to their corporate email addresses. Top-clicked subjects in this category also include Facebook and Twitter notifications, message alerts and login alerts.
The Top 10 Most-Clicked Phishing Email Subjects
- Password Check Required Immediately
- Revised Vacation & Sick Time Policy
- COVID-19 Remote Work Policy Update
- COVID-19 Vaccine Interest Survey
- Important: Dress Code Changes
- Scheduled Server Maintenance -- No Internet Access
- De-activation of email in Process
- Test of the company_name Emergency Notification System
- Scanned image from MX2310U@domain
- Recent Activity Report
Key Takeaway
Hackers are playing into employees' desires to remain security minded. Password management is a popular way to get people to click on a link. Hackers also play into employees' emotions, causing them to panic when they see a de-activation of email in process. And who can resist HR-related messages that could potentially affect the daily work of employees.
Common In the Wild Phishing Attacks
- Microsoft 365: Scheduled Server Backup
- IT: IT-Help Ticket Survey Invitation
- Warning: Your E-mail account has just sent 260 E-Mails
- Amazon Prime: Action required - Card on file has been declined
- License Update
- Google: Take action to secure your compromised passwords
- Apple: Prize winner! We need your confirmation
- Zoom: You missed a Zoom meeting
- HR: Your payroll details needs updating
- Facebook: Important message regarding your Facebook profile
Key Takeaway
The common theme we see here is the push for action required. Cybercriminals are preying on heightened stress, distraction, urgency, curiosity, and fear in users. These types of attacks are effective because they cause a person to react before thinking logically about the legitimacy of the email.
The reality is, companies are simply not doing enough to reduce the risks associated with phishing and malicious software. If your company is looking to take it a step further, Rhyme can help you with remote monitoring and management of your network to be more proactive in preventing phishing and similar attacks. Should you fall victim to a phishing attack, Rhyme would have a reliable backup and disaster recovery (BDR) solution in place to ensure your essential data can be restored with as little downtime as possible.
Contact us today for more information.
Resource: https://www.knowbe4.com/phishing
For more information on phishing attack see:
Avoiding Social Engineering and Phishing Attacks