Cyber Security is an ever-changing landscape that requires constant monitoring and adaptation. Hackers and malicious users are always looking for new ways to gain access to your sensitive information, and some of these newer methods may be ways you’ve never considered before. Here are 8 cyber security tips to keep you and your business safe this holiday season.

With the holiday season kicking off, many people are going to be turning online to do their shopping. Black Friday and Cyber Monday deals are great places to save, however, they’re also perfect opportunities for hackers to attempt to steal your information and scam you. Here are some tips on how to stay safe while shopping online.
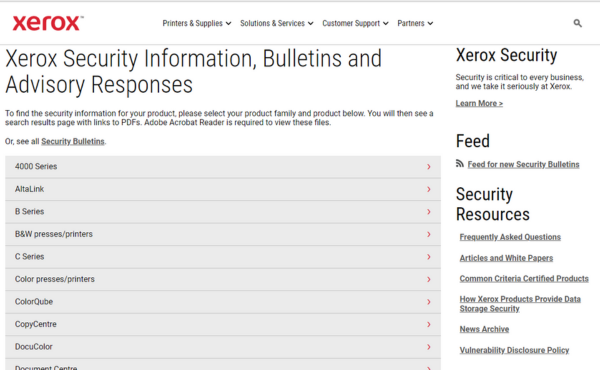
October is National Cybersecurity Awareness Month which makes it a great time to share some security tips and information. For example, did you know that Xerox has a webpage dedicated to security information for all their devices? Let’s take a look at what you can expect to see on this webpage.

Sharp recently announced their partnership with Bitdefender, a leader in the cybersecurity industry, which will bring cybersecurity in MFPs to a whole new level. Printers and MFPs are often overlooked when it comes to cybersecurity despite their importance, and this partnership will ensure that those devices and your network are protected.

As technology and solutions continue to lead more towards the cloud, it’s important to understand hesitations that SMBs might have to adopting a cloud-based solution themselves. Often, SMBs hold fears and misconceptions toward solutions that leverage the cloud that ultimately hold them back from starting their cloud journey. What are these misconceptions and fears, and how can a cloud-based solution benefit your SMB?

Understanding how malware works and what vulnerabilities it attempts to manipulate is an important part of cyber security. We asked our Director of IT to shed some light on what malware is, and how organizations can defend against it.

Keeping your company and information secure is a top priority as cyberattacks aren’t going anywhere soon. Whether it be malware, ransomware, phishing, or social engineering, cyberattacks can occur at any time and can lead to huge expenses to resolve. Because of this, many companies are considering Cyber Liability Insurance to help combat this, but what exactly is cyber liability insurance, and what does it cover?

Video calls are abundant with opportunities to compromise your private information. Follow these tips to help form safe video call practices to protect yourself from slip ups or malicious acts from others.

A well-balanced, multi-layered security strategy is needed to help ensure your copiers and printers keep your information safe from malicious intruders. Sharp MFPs are equipped with multiple security features to do just that.

Businesses today require more work in less time with fewer resources. But fortunately, with smart office technology employees can work smarter and more productively, and not cut into valuable family time. Smart offices are an opportunity to improve production, employee morale and provide a competitive edge for your business.
The Cybersecurity & Infrastructure Security Agency has the top tips for safely using videoconferencing to ensure employees are only using approved tools and that their home networks are secured.

After rapidly adopting wide-scale remote work practices in response to COVID-19, organizations have started planning for more permanent and strategic teleworking postures. An organization’s executive leaders, IT professionals, and teleworkers all have roles to play in the shift from temporary to long-term or permanent telework strategies.

Remote work is not new but may be unfamiliar to some employees, leaders and businesses. With significant rise in temporary work from home, it is important to think about security and keeping your home network security as strong as the office network security.

Is technology at the top of your priority list? At Rhyme we help businesses develop their technology strategy, implement that strategy and then support it through its lifecycle. Our goal is to help your business grow by increasing profits and lowering risk. Evaluate these five risks to decide if your technology needs more attention.

What is the dark web and how do you protect yourself? The dark web is a place where criminals buy and sell stolen personal information, such as credit card numbers, bank account passwords, and even Social Security numbers. Unfortunately, like most things on the internet, once the information is out there, it can’t be erased.

Businesses face significant financial loss when a cyber attack occurs. In 2018, the U.S. business sector had the largest number of data breaches ever recorded: 571 breaches. Cybercriminals often rely on human error—employees failing to install software patches or clicking on malicious links—to gain access to systems.

The line between our online and offline lives is indistinguishable. In these tech-fueled times, our homes, societal well-being, economic prosperity and nation’s security are impacted by the internet.

Though document management sounds like a complicated process that’s reserved for large corporations, it’s actually something that every business – of every size – does every day. In fact, your office is doing it right now as we speak.
On January 14, 2020, support for Windows Server 2008 and 2008 R2 will end. That means the end of regular security updates. Don't let your infrastructure and applications go unprotected. We're here to help you migrate to current versions for greater security, performance and innovation.

If technology gives your organization a competitive edge, you are familiar with how expensive it is to keep it current. Now, consider that at times, the purchase price of your technology is only a fraction of the cost of the total cost of ownership.

Disasters can happen to any business at any time and the downtime they cause is truly catastrophic, many of which never recover. The strength to avert disasters and effectively handle the ones that occur starts with knowledge.

Don't fall for another phishing attack. More than 96% of phishing attempts arrive by email. Phishing is a threat to every organization across the globe.

Not really sure what a backup is? Don’t worry you’re not alone, over 30% of people never backup their files. A backup is a second copy of all your important files. Instead of storing it only on your computer, you keep another copy of everything somewhere safe, at an off-site location.

It can happen to the best of us—your shiny new phone, tablet or laptop, left in an airplane seat pocket or stolen at the local coffee shop when you got up for a refill. Imagine losing the device that connects you to the outside world, and most importantly, your work.

Malicious emails coupled with a general lack of employee cyber security training is the leading cause of a successful ransomware attack. Ransomware is a type of malware that infects computer systems, restricting users’ access to the infected systems and has become the most prominent global threat to business cyber security today.

Did you know that the applications you use every day, from payroll to invoicing, could be running on Windows Server 2003? Microsoft is ending support for the 2003 version of Windows Server on July 14, 2015 and it's time to find out if your business is at risk.

Technology has revolutionized the way we communicate. We create, share and store data faster than ever and this has greatly impacted the way we conduct business. While transmitting data almost instantaneously has its benefits, it also causes security concerns, especially for businesses that require their information to be confidential and safe.

With the unlimited amount of phone calls and emails you receive a day it can be hard to keep track of who you talked to and what they do for you. Scammers take advantage of this and use it for their own benefit. You can’t protect yourself if you are not aware of the variety of different schemes some people will throw at you.

Small businesses are faced with difficult technology questions every day, like what technology should I invest in, what technology should have a priority over another or what gives my business a competitive advantage?